It has been over a month since my last post - life has been very busy at work and at home! I still have 3 posts left on my Windows Firewall with Advanced Security to-do list, and a building list of posts about Windows Event Forwarding, or "How I learned to stop worrying and love endpoint logs". So, with that said, let's chip off another topic from my WFwAS list.
I have hinted at this a few times through several posts, but there are several things that Windows Firewall with Advanced Security doesn't do well. Let's face it - the technology is more or less 10 years old. Aside from the ability to tie traffic to a specific application (which is a big deal by the way, in case you haven't read my other posts) it is essentially a basic layer 4 firewall. There are some significant scenarios where WFwAS starts to show its age. It is still useful, applicable, and with the right tools to assist even manageable. But there are a few limitations that have to be worked around if it is going to be used successfully. Here are a few specifics, in no particular order, of things that it doesn't do well.
1. When writing rules there are often limitations encountered when needing to allow or block CDNs with huge swaths of IP space. The internet started using DNS oh, something like 1984 - a mere 32 years ago. Why? Because IP addresses don't scale!
<rant>
Yet this firewall, sitting there humming away happily next to the DNS resolver client behaves in a very anti social manner and instead of asking a few simple questions that the DNS resolver would be happy to answer it goes on its own and instead is based simply off of IP address ranges.
<sarcasm>
I'm not bitter - not at all.
</sarcasm>
Don't even get me started on IPv6. Pity the poor being that has to use this to limit access to IP6 and the think of the massive amounts of electrons that would have to be inconvenienced to make it happen. Or not - because even though it can be used with IPv6, I doubt it is very much.
</rant>
Because of DNS, resource to IP addresses mapping can be umm, dynamic. They can change quickly, they can be load balanced, etc. Static lists of IPs don't always map to a resource I want to allow or deny and if it does now, it might not later, and then might all over again.
Network firewall vendors have heard this loud and clear from their customers and adapted to stay relevant, but WFwAS hasn't. Something like PowerShell can be used to create more dynamic lists that are then imported into the configuration (a topic for a future post), and the firewall itself seems to handle very large lists with ease, but this is bolting on a compensation and can be clunky.
Mitigating control: Use a web proxy or more advanced edge firewall to assist with this where it can.
2. Applications with dynamic names are difficult to manage. Applications have to be explicitly defined, there are no options for wildcards in the path. This makes it difficult to write rules for applications that might need to be allowed, like notorious collaboration "meeting go to" apps or "web ex perience" executables that are saved to temp folders with seemingly random executable names connecting to seemingly random IP addresses. Either a full firewall allow list has to be implemented, denying anything unknown (which can be a management headache); or a block list has to be configured and any unknown application has to be allowed.
Mitigating control: Use application controls (such as AppLocker or better, Device Guard or a 3rd party application control tool if you have it available) to limit what applications can be run on a system and use WFwAS to mitigate the most commonly allowed and abused apps.
3. Some applications seem to use addresses scattered all over the entirety of the IPv4 address space! For example, web browsers and HTML email clients connect to seemingly random IP addresses all day long. This is related to item #1. I wouldn't recommend limiting these applications with WFwAS in any but the most restrictive environments, and even then they are probably sufficiently covered by egress allow lists at the network edge.
Mitigating control: Allow any destination IP for apps that are required to interact with the internet as part of their primary functionality. WFwAS can be used to control the ports that these apps have access to, but I wouldn't recommend anything beyond that. Rely on other defenses to help you here.
4. What if there was this scenario where someone could use crazy archaic technology X [such as - oh I don't know - using something like PowerShell to instantiate a COM call to IE to masquerade as an application allowed to get to any IP to do my CnC] to skirt through your list of allowed applications and Endpoint Firewall all in one fell swoop? Ha! All your base are belong to us!
Mitigating control: Don't allow COM capable apps outside of your internal IP range. Like Internet Explorer. Seriously - use a different browser for web browsing. That said, I understand that a stunt like enforcing this policy would raise a few eyebrows at a corporate scrum or change control meeting. I am still investigating other ways to interrupt COM calls where they are not needed, but haven't found anything magical yet. If anyone has, I would love to hear it.
All these things said I still think that this is an effective control that I have been able to demonstrate in a lab and production environments stops malware and malicious activity that few other tools can. This control doesn't function as a "silver bullet" to solve almost all security needs. It solves one or two things very well, but must exist in an ecosystem of other tools to provide a layered approach of security.
I hope to discuss some of these mitigating controls much more in depth in a future post.
Until then, work hard and spend time with your family.
Branden
@limpidweb
Monday, December 19, 2016
Tuesday, November 8, 2016
To Centralize or Not To Centralize
In my last post I discussed how Windows Filtering Platform auditing can generate the necessary log records for creating outbound rule sets, continuing my theme of applying outbound restrictions to specific applications that are abused to bypass mitigations such as pre-defined application allow lists. With this audit configuration, along with a rule set that defaults to allow and doesn't have any block entries, machines can run for a while to start generating a list of IP addresses to allow.
While that is simmering on the back burner now is a good time to think about how we would like to deploy should we choose to accept this mission (how's that for mixing metaphors?). There are two methods that I am aware of that this can be configured.
Pros and Cons
Choosing which method (or even a combination of the two) to deploy depends on the needs of the environment. It is possible to use Local or GPO, as well as GPO with a merge of a local policy. I can't think of a scenario where I would ever want to use the merge option - I usually disable that capability by removing the selection for "Allow local firewall rules". (This can be found by selecting a profile in a GPO configuration, selecting "Customize...", and under "Rule merging" setting "Apply local firewall rules" to "No").
So which one works best in a corporate environment? I think that local policies carry some very substantial risks.
When all of these are combined the result is an unpredictable and difficult to manage firewall configuration that I wouldn't recommend in a corporate environment.
That said, there are two critical cons to using GPOs that must be considered and mitigated appropriately if this deployment method is used.
If appropriately configured (not allowing local rule merging) and tested, a GPO can be much more difficult to bypass or disable and can be implemented safely and effectively. This raises the difficulty and cost for attackers, forcing them to abandon many of the mechanisms that are used with malware today.
That said, if admin rights are obtained it could be possible to disable the firewall regardless of the chosen deployment method. At that point it would also be possible (and maybe easier) to just overwrite or attack a permitted application than trying to disable the firewall.
A lot of this hinges on obtaining local admin rights. If end users are browsing the internet and using office productivity applications with local admin privileges there are many options for getting around this (and many other) controls regardless of how they are applied. It is also important to apply security patches in a timely manner to limit the ability of code to elevate privileges using exploits. Windows Firewall with Advanced Security outbound controls can only work if they are a part of a larger ecosystem of controls that work in concert. I believe these outbound controls (or any endpoint firewall with this type of capability) are a critical part of the ecosystem, but can't stand without it.
Until then, work hard and spend time with your family.
Branden
@limpidweb
While that is simmering on the back burner now is a good time to think about how we would like to deploy should we choose to accept this mission (how's that for mixing metaphors?). There are two methods that I am aware of that this can be configured.
- Local workstation policy
- Group Policy
I think that there are benefits and disadvantages to both approaches, so they are both worth some consideration. I have yet to run into any feature differences when deploying it GPO vs. locally (or vice-versa), but I do think that there are some tactical advantages to using GPOs. If GPOs aren't available to you (for example, home/standalone computers or a workgroup) then a local configuration still provides benefit beyond having nothing at all.
Local Policy
This is where I started getting my feet wet when working with Windows Firewall with Advanced Security. The biggest benefit to me at the time was that if I misconfigured something it only affected my test device and I had direct access to the machine to undo any changes. It allowed me to experiment and verify rules worked as expected while getting comfortable with the options and interface.
The local firewall policy can be configured using the MMC console. This can be opened in several ways, here are two:
- Control Panel > System and Security > Windows Firewall > Advanced Settings
- MMC Console > File - Add/Remove Snap-in... > Windows Firewall with Advanced Security - Add > Local Computer - Finish.
(Note: depending on the settings on your computer, these will only work if you have access to a local administrator account and/or with UAC elevation.)
Once the GUI is open we have the ability to add or remove rules that affect the local computer. If necessary the policy can be created and then exported, allowing us to import it on another computer or back it up in case it needs to be restored.
Group Policy
The GPO configuration can be managed with the Group Policy Management utility. A new group policy has to be created or an existing one edited. Right click the policy to be modified, and then navigate to Computer Configuration > Policies > Windows Settings > Security Settings > Windows Firewall with Advanced Security. This GUI is very similar to the local configuration.
When making GPOs it can be helpful to create multiple firewall specific GPOs that have similar rule sets depending on the security requirements of the machines that they are applied to. These can then be selectivly applied using WMI filters or security filters, but this won't work in some environments so YMMV.
When making GPOs it can be helpful to create multiple firewall specific GPOs that have similar rule sets depending on the security requirements of the machines that they are applied to. These can then be selectivly applied using WMI filters or security filters, but this won't work in some environments so YMMV.
Pros and Cons
Choosing which method (or even a combination of the two) to deploy depends on the needs of the environment. It is possible to use Local or GPO, as well as GPO with a merge of a local policy. I can't think of a scenario where I would ever want to use the merge option - I usually disable that capability by removing the selection for "Allow local firewall rules". (This can be found by selecting a profile in a GPO configuration, selecting "Customize...", and under "Rule merging" setting "Apply local firewall rules" to "No").
So which one works best in a corporate environment? I think that local policies carry some very substantial risks.
- If malicious code executes on a machine and is able to obtain admin privileges it can create policy rules allowing the traffic out or turning the firewall off and bypassing restrictions.
- Local policies can also be changed by local administrators, allowing them to turn it on or off or add/remove rules which can quickly lead to configuration drift.
- A lot of programs will also create very liberal outbound policies when they are installed.
When all of these are combined the result is an unpredictable and difficult to manage firewall configuration that I wouldn't recommend in a corporate environment.
That said, there are two critical cons to using GPOs that must be considered and mitigated appropriately if this deployment method is used.
- If it is misconfigured, outbound GPOs can prevent machines from receiving future GPOs and prevent them from communicating with critical services. This is probably the largest deterrent to using this technology and would probably be a resume generating event in most environments. It is why I spent so much time focusing on the block list capabilities with inverse ranges that I talked about in a previous post.
- There is a psuedo-random delay (sometimes up to several hours) between when a change is made to the policy and when it takes affect on an endpoint. This could be a problem if something needed to be rolled out rapidly.
If appropriately configured (not allowing local rule merging) and tested, a GPO can be much more difficult to bypass or disable and can be implemented safely and effectively. This raises the difficulty and cost for attackers, forcing them to abandon many of the mechanisms that are used with malware today.
That said, if admin rights are obtained it could be possible to disable the firewall regardless of the chosen deployment method. At that point it would also be possible (and maybe easier) to just overwrite or attack a permitted application than trying to disable the firewall.
A lot of this hinges on obtaining local admin rights. If end users are browsing the internet and using office productivity applications with local admin privileges there are many options for getting around this (and many other) controls regardless of how they are applied. It is also important to apply security patches in a timely manner to limit the ability of code to elevate privileges using exploits. Windows Firewall with Advanced Security outbound controls can only work if they are a part of a larger ecosystem of controls that work in concert. I believe these outbound controls (or any endpoint firewall with this type of capability) are a critical part of the ecosystem, but can't stand without it.
Regardless of which method is chosen for deployment, PowerShell is has been my friend. Both local and group policies can be directly created, viewed, edited, and deleted with PowerShell. This allows routine tasks to be saved as scripts (for example, modifying the destination IP allowed list to accomodate for a previously unseen destination or removing a destination IP that is no longer necessary). Large lists of IP addresses can be maintaned as files and then imported with PowerShell and applied to the appropriate policy, saving time and difficulty navigating these in the GUI.
I plan to cover PowerShell specifics in a future post - it has saved me an immense amount of time and allowed me to scale and deploy this as a mitigation tool where it otherwise wouldn't have been practical.
I plan to cover PowerShell specifics in a future post - it has saved me an immense amount of time and allowed me to scale and deploy this as a mitigation tool where it otherwise wouldn't have been practical.
Until then, work hard and spend time with your family.
Branden
@limpidweb
Monday, October 31, 2016
Audit Logs, XML Filters, and PowerShell, Oh My!
My last post documented the big breakthrough for me - being able to limit internet access for a few specific programs that had little business accessing the internet and were being abused by malware, pen testers, and researchers alike. Now I had a flexible tool that I could use to greatly limit this abuse.
Now what do I do with it?
Initially I thought it would be sufficient to allow all inside network access for the applications that I chose to limit and then just allow internet access as needed. I had a policy ready to go that would enforce this, but after some initial testing I learned that there was more activity by these applications than I initially thought. To deploy this it would be critical to log connections in the production environment and collect the information needed to make informed baselines before enforcing any application specific rules.
Easy enough, there was a place in the policy configuration where I could set up a log file which would output to a simple text file.
Looks pretty straight forward. Once the configuration was enabled I browsed to the log file to see what I had to work with. Here is a sample:
My heart sank. There is some useful information in this log, but the application entry was missing! The key feature that drove me to use this tool was the fact that it could be configured to control application access to IP addresses. In order to effectively do that without the rollout becoming a resume generating event I needed a candidate configuration that allowed everything, but logged it, so I could create a baseline; and this wasn't going to let me do that. The other piece of information that this was missing was the rule that it matched against. Lots of data, but nothing to see here. I disabled this log and moved on.
After some time searching I found something that had potential: Windows Filtering Platform Auditing. Windows Filtering Platform is a set of services and an API in the Windows OS that allows traffic to be filtered. It is the underlying set of features that Windows Firewall with Advanced Security runs on top of. (For more, see MSDN) Auditing can be enabled by a policy located in the following areas:
Local:
Local Security Policy\Security Settings\Advanced Audit Policy Configuration\System Audit Policies - Local Group Policy Object\Object Access
GPO:
Computer Configuration\Policies\Windows Settings\Security Settings\Advanced Audit Policy Configuration\Audit Policies\Object Access
In these audit policies there is a subcategory for Audit Filtering Platform Connection. If Success and Failure are configured for this subcategory an event will be created in the system Security log with information about both blocked (event ID 5157) and allowed (event ID 5156) connections. These logs are much more detailed, including the following information:
...and a handful of other pieces of information. Having this information allows us to create a policy that allows all connections but audits them. We can then go through the audit logs and use them to determine a baseline to use when creating our application rules - of course only after thoroughly vetting the source application and every destination IP... right?
These logs have the type of information I was only able to dream about when working with network firewalls - with those I could trace traffic back to a machine and make a good guess at which user it was from but that was about the limit of what I could do. Seeing these logs takethe username from the credentials used to launch a process along with the process name and path is a dream come true and provides valuable troubleshooting and forensics data that can be analyzed and consumed later.
Now that we have the data we need, how do we make use of it? On a single computer this is pretty straight forward. These audit settings generate a large volume of events (size log files for retention appropriately), but can be quickly filtered in or out of the event viewer console with the basic filter or with the XML filters.
For example, if you can find a sample event for an application you would like to write a rule for, an XML filter can be used to limit the packets to just what matches one or a few fields. Here is part of the XML view of an event where chrome.exe is connecting to www.google.com over port 443:
The fields that are shown can be used in the XML filter to get only the specific log entries we might be looking for, even allowing us to use things like =, !=, multiple matches with AND/OR, etc. (see this TechNet blog for more info). I have been able to use up to 7 conditions to narrow down what I was looking for. (As a side note, more than 7 conditions seems to cause the filter to start behaving unexpectedly, but I can't find any information on why that is. If anyone knows why I would be very interested in hearing it.)
But let's not stop there! GUIs don't scale well. Let's imagine we would like to automate this process and have it generate some interesting data for us across thousands of machines so that we could build a GPO and have the confidence to enforce it! I ♥ PowerShell for this - "Get-WinEvent" with the "FilterXPath" switch allows us to write this all in a script to generate a match and then output it to a file for later consumption. If we use an event centralizing technology like Windows Event Forwarding then we have all of these logs in one place and the tools to make them useful! If we have access to a SIEM or logging platform that can take the logging hit, we have a recipe for large scale success.
Hopefully more on Get-WinEvent, WEF, and maybe event ELK in the next couple of posts.
Until then, work hard and spend time with your family.
Branden
@limpidweb
Now what do I do with it?
Initially I thought it would be sufficient to allow all inside network access for the applications that I chose to limit and then just allow internet access as needed. I had a policy ready to go that would enforce this, but after some initial testing I learned that there was more activity by these applications than I initially thought. To deploy this it would be critical to log connections in the production environment and collect the information needed to make informed baselines before enforcing any application specific rules.
Easy enough, there was a place in the policy configuration where I could set up a log file which would output to a simple text file.
Looks pretty straight forward. Once the configuration was enabled I browsed to the log file to see what I had to work with. Here is a sample:
 |
| What's missing here? |
After some time searching I found something that had potential: Windows Filtering Platform Auditing. Windows Filtering Platform is a set of services and an API in the Windows OS that allows traffic to be filtered. It is the underlying set of features that Windows Firewall with Advanced Security runs on top of. (For more, see MSDN) Auditing can be enabled by a policy located in the following areas:
Local:
Local Security Policy\Security Settings\Advanced Audit Policy Configuration\System Audit Policies - Local Group Policy Object\Object Access
GPO:
Computer Configuration\Policies\Windows Settings\Security Settings\Advanced Audit Policy Configuration\Audit Policies\Object Access
In these audit policies there is a subcategory for Audit Filtering Platform Connection. If Success and Failure are configured for this subcategory an event will be created in the system Security log with information about both blocked (event ID 5157) and allowed (event ID 5156) connections. These logs are much more detailed, including the following information:
Source User IDEdit 5/9/2017: After additional research I have learned that the source user ID is not in these logs. :-(- Process ID
- Application Name and Path
- Direction
- Source Address/Port
- Destination Address/Port
- Protocol
- Filter Run-Time ID (rule ID match)
...and a handful of other pieces of information. Having this information allows us to create a policy that allows all connections but audits them. We can then go through the audit logs and use them to determine a baseline to use when creating our application rules - of course only after thoroughly vetting the source application and every destination IP... right?
These logs have the type of information I was only able to dream about when working with network firewalls - with those I could trace traffic back to a machine and make a good guess at which user it was from but that was about the limit of what I could do. Seeing these logs take
Now that we have the data we need, how do we make use of it? On a single computer this is pretty straight forward. These audit settings generate a large volume of events (size log files for retention appropriately), but can be quickly filtered in or out of the event viewer console with the basic filter or with the XML filters.
For example, if you can find a sample event for an application you would like to write a rule for, an XML filter can be used to limit the packets to just what matches one or a few fields. Here is part of the XML view of an event where chrome.exe is connecting to www.google.com over port 443:
 |
| This can be obtained by opening the event in the Security event log, selecting the Details tab, and then selecting the "XML View" radio button. |
The fields that are shown can be used in the XML filter to get only the specific log entries we might be looking for, even allowing us to use things like =, !=, multiple matches with AND/OR, etc. (see this TechNet blog for more info). I have been able to use up to 7 conditions to narrow down what I was looking for. (As a side note, more than 7 conditions seems to cause the filter to start behaving unexpectedly, but I can't find any information on why that is. If anyone knows why I would be very interested in hearing it.)
But let's not stop there! GUIs don't scale well. Let's imagine we would like to automate this process and have it generate some interesting data for us across thousands of machines so that we could build a GPO and have the confidence to enforce it! I ♥ PowerShell for this - "Get-WinEvent" with the "FilterXPath" switch allows us to write this all in a script to generate a match and then output it to a file for later consumption. If we use an event centralizing technology like Windows Event Forwarding then we have all of these logs in one place and the tools to make them useful! If we have access to a SIEM or logging platform that can take the logging hit, we have a recipe for large scale success.
Hopefully more on Get-WinEvent, WEF, and maybe event ELK in the next couple of posts.
Until then, work hard and spend time with your family.
Branden
@limpidweb
Monday, October 10, 2016
The Key to Success - Enabling Blocklists with Inverse Ranges
Have you ever been doing some task and have some random connection happen in the back of your mind regarding a completely unrelated subject and leaving you with no idea how it happened? That is what happened to me after my initial roadblock when trying to configure Windows Firewall with Advanced Security (WFwAS) to limit internet access for some applications. I knew that if it could control applications in this way it would mitigate all sorts of app AppLocker bypasses and quite a bit of malware. I had shelved my work on the matter though, until I had one of these particular random connection events happen to me while I happened to be taking a shower.
To recap my last post, I had been looking into the ability of WFwAS to limit access to IP addresses or ranges based off of individual executables, but ran into a dead end with the peculiar way that it handles rule order of operations. I didn't yet have enough data or comfort with the tool to deploy it in a way that only allowed pre-defined applications to my entire organization, and had to shelve my active work on it because I couldn't find another way to deploy it. If only I had a way to block some high risk applications that I was pretty sure had little legitimate internet use!
So there I was washing my hair in the shower, and then it hit me. "What if I block all IP addresses except the range that I want to allow, and then just configure the default rule to 'Allow' to handle the rest?" I thought it through for a little while and realized that this could be the key to solving my problem!
After that I couldn't wait to get to work and when I did I jumped right in and started setting it up on my test machine. Sure enough it behaved as expected and worked immediately! Unable to contain myself I bubbled over and had to share my success with a coworker who had been patiently listening to my drama about Windows' firewall. The key to the whole thing was something I called "inverse ranges". But what were these "inverse ranges"? To understand that, let's look back at the example from my last post.
My last post illustrated why this wouldn't work with WFwAS. To overcome this I had to think outside of the allow range and instead take the same end goal (blocking the stuff I didn't trust, allowing the stuff I have to trust) and make it fit in the WFwAS "process blocks first" mentality.
The key for this was to block what was not allowed, and then default allow to permit the rest.
Here is the logic spelled out:
Technically this could be done with subnet ranges, but I decided to simplify my rules by taking advantage of a WFwAS feature by using basic start-finish ranges. This allowed me to take what would require quite a few subnet statements and put it into a single basic range and greatly simplify managing my rule sets.
That's it, my secret is out. Isn't that cool? Well, I think it is anyway. I was able to get a successful PowerShell web download from a server on my allowed range (my internal network), but when I tried something from the internet that was previously working it puked red text onto my console window. But this time it was a welcomed and good puking of red text... in a twisted sort of way where my anthropomorphisation of a consoles behavior begins to quickly fall apart. Because it wasn't just my command puking; no, it was every piece of malware and crypto ransomware that used PowerShell to do its dirty deeds that would be puking all over consoles that were running hidden, and that could now be ignored and left to suffer alone in a world of STDERR!!!
So my next task was to take this and apply it to one of my original goals. I wanted to mitigate Casey Smith's clever use of system utilities to download code from the internet and execute it while bypassing application AppLocker. So I went over to his GitHub page and decided to create a rule for each item on his list of AppLocker techniques that used an executable to download code. I couldn't stop them from executing, but I could substantially limit their capabilities by limiting which IP addresses they needed access to.
I wrote up rules that covered the 32 and 64 bit locations for the utilities on the list and then proceeded to test it in our environment. There were a few applications that did have legitimate needs to access IP address space outside of my organization, but it was easy enough to just add in the appropriate "inverse ranges" to the block statements. There were a few challenges to be sure, but I had an effective mitigation that covered a wide swath of malicious activity. It would be worth my time to continue down this path and see how far it would take me.
With the basic functionality operating, I now had to tackle the challenges presented by long lists of IP addresses across multiple rules. To top that off, several of my applications were running up against the bane of many a firewall administrator - large lists of IP space owned by companies such as Microsoft, Amazon, and Akamai. I decided to tackle it, but that will have to wait until a future post for details.
I really hope that others see the benefit in this and find it helpful. Sound off in the comments or on Twitter if you have any questions about it. I plan to have more good things to come!
Until then, work hard and spend time with your family.
Branden
@limpidweb
To recap my last post, I had been looking into the ability of WFwAS to limit access to IP addresses or ranges based off of individual executables, but ran into a dead end with the peculiar way that it handles rule order of operations. I didn't yet have enough data or comfort with the tool to deploy it in a way that only allowed pre-defined applications to my entire organization, and had to shelve my active work on it because I couldn't find another way to deploy it. If only I had a way to block some high risk applications that I was pretty sure had little legitimate internet use!
So there I was washing my hair in the shower, and then it hit me. "What if I block all IP addresses except the range that I want to allow, and then just configure the default rule to 'Allow' to handle the rest?" I thought it through for a little while and realized that this could be the key to solving my problem!
After that I couldn't wait to get to work and when I did I jumped right in and started setting it up on my test machine. Sure enough it behaved as expected and worked immediately! Unable to contain myself I bubbled over and had to share my success with a coworker who had been patiently listening to my drama about Windows' firewall. The key to the whole thing was something I called "inverse ranges". But what were these "inverse ranges"? To understand that, let's look back at the example from my last post.
 |
| This type of rule is what I spent years configuring and is what defined how my mind thought about rule sets. |
The key for this was to block what was not allowed, and then default allow to permit the rest.
Here is the logic spelled out:
- Rule to block IP ranges not allowed that were before the IP address range I want to allow.
- Rule to block IP ranges not allowed that were after the IP address range I want to allow.
- Default allow the rest.
In other words define what I don't want and assume what I do want, thus the "inverse". Block what I want to block, the default allow permits the rest.
Let's take a look at what that looks like in our WFwAS configuration. I will use the 64bit version of PowerShell.exe as an example, and deny it to everything but RFC1918 IP address space. After watching our pen testers, studying malware in my test lab, and reading other people's blogs I knew that this was becoming a common method used by criminals to use initial execution on a machine to download and execute malicious code and would be high on my list to mitigate. As cool as that sounds, it was probably also due in large part to PowerShell web connections being one of the few things I could actually reproduce for testing that still had real world application.
(I apologize for the picture roll, especially if you are reading this on a mobile device).
Let's take a look at what that looks like in our WFwAS configuration. I will use the 64bit version of PowerShell.exe as an example, and deny it to everything but RFC1918 IP address space. After watching our pen testers, studying malware in my test lab, and reading other people's blogs I knew that this was becoming a common method used by criminals to use initial execution on a machine to download and execute malicious code and would be high on my list to mitigate. As cool as that sounds, it was probably also due in large part to PowerShell web connections being one of the few things I could actually reproduce for testing that still had real world application.
(I apologize for the picture roll, especially if you are reading this on a mobile device).
 |
| Key here is that it is enabled and the Action is set to "Block the connection". A reasonable name helps too. |
 |
| Here is the "inverse range" concept in action. Look closely at the IPs and remember that these are being blocked. |
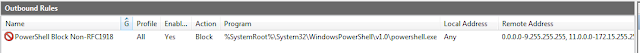 |
| Hard to see, and can't get it all on a single shot, but here is what part of the rule looks like after being configured. |
That's it, my secret is out. Isn't that cool? Well, I think it is anyway. I was able to get a successful PowerShell web download from a server on my allowed range (my internal network), but when I tried something from the internet that was previously working it puked red text onto my console window. But this time it was a welcomed and good puking of red text... in a twisted sort of way where my anthropomorphisation of a consoles behavior begins to quickly fall apart. Because it wasn't just my command puking; no, it was every piece of malware and crypto ransomware that used PowerShell to do its dirty deeds that would be puking all over consoles that were running hidden, and that could now be ignored and left to suffer alone in a world of STDERR!!!
So my next task was to take this and apply it to one of my original goals. I wanted to mitigate Casey Smith's clever use of system utilities to download code from the internet and execute it while bypassing application AppLocker. So I went over to his GitHub page and decided to create a rule for each item on his list of AppLocker techniques that used an executable to download code. I couldn't stop them from executing, but I could substantially limit their capabilities by limiting which IP addresses they needed access to.
I wrote up rules that covered the 32 and 64 bit locations for the utilities on the list and then proceeded to test it in our environment. There were a few applications that did have legitimate needs to access IP address space outside of my organization, but it was easy enough to just add in the appropriate "inverse ranges" to the block statements. There were a few challenges to be sure, but I had an effective mitigation that covered a wide swath of malicious activity. It would be worth my time to continue down this path and see how far it would take me.
With the basic functionality operating, I now had to tackle the challenges presented by long lists of IP addresses across multiple rules. To top that off, several of my applications were running up against the bane of many a firewall administrator - large lists of IP space owned by companies such as Microsoft, Amazon, and Akamai. I decided to tackle it, but that will have to wait until a future post for details.
I really hope that others see the benefit in this and find it helpful. Sound off in the comments or on Twitter if you have any questions about it. I plan to have more good things to come!
Branden
@limpidweb
Monday, October 3, 2016
Second fail brings me closer...
To recap my last post, I was trying to limit the ability of individual applications on domain workstations from being abused to bypass other restrictions (such as application allow lists) to download malicious content from the internet. EMET provided the capability to do this with an on/off switch, but I needed something more granular to roll this out at scale.
I knew that Windows Firewall with Advanced Security (hereafter WFwAS) was capable of limiting access by application, but I had only worked with it to limit traffic inbound to a workstation, which is the capability that the basic Windows Firewall has had since Windows XP SP2. I hadn't spent much time with the new features introduced in Windows Vista when the name was appended "with Advanced Security". So, I thought I would give it a go.
I began looking into the Outbound Rules section of the configuration. I was immediately overwhelmed with a very long list of complicated rules. Microsoft had contributed helpful stuff they thought I would need. In addition, all sorts of apps had put in custom rules, usually allowing various applications access to any IP address with any protocol. This would have to be cleaned up. But, the one key thing was here. There are rules that were allowing outbound traffic with specific applications listed in the rule. So far this was looking very promising!
Now that I knew that the rules could be limited to outbound traffic from specific applications, the next problem to tackle was limiting an application to some approved destination and then blocking it from all of the rest. My mind immediately went to my past as a network firewall admin... this was a problem that I learned to solve back in my Cisco Network Academy days when my instructors drilled IOS ACLs into our heads.
Turns out there is a way to do what I wanted, but I had to stop thinking like a firewall admin and think outside of the allow range. But, this post is already longer than I expected, so I will plan to go over how that was accomplished next week. I'll see if I can keep a cadence of a post a week.
Until then, work hard and spend time with your family.
Branden
@limpidweb
I knew that Windows Firewall with Advanced Security (hereafter WFwAS) was capable of limiting access by application, but I had only worked with it to limit traffic inbound to a workstation, which is the capability that the basic Windows Firewall has had since Windows XP SP2. I hadn't spent much time with the new features introduced in Windows Vista when the name was appended "with Advanced Security". So, I thought I would give it a go.
 |
| To give a frame of reference, here is the console for WF on Windows 10 |
I began looking into the Outbound Rules section of the configuration. I was immediately overwhelmed with a very long list of complicated rules. Microsoft had contributed helpful stuff they thought I would need. In addition, all sorts of apps had put in custom rules, usually allowing various applications access to any IP address with any protocol. This would have to be cleaned up. But, the one key thing was here. There are rules that were allowing outbound traffic with specific applications listed in the rule. So far this was looking very promising!
Now that I knew that the rules could be limited to outbound traffic from specific applications, the next problem to tackle was limiting an application to some approved destination and then blocking it from all of the rest. My mind immediately went to my past as a network firewall admin... this was a problem that I learned to solve back in my Cisco Network Academy days when my instructors drilled IOS ACLs into our heads.
- Allow traffic from a source IP/range to a destination IP/range
- Deny all traffic from the source IP/range to ANY
- Continue with rest of list
- Default Deny statement at the end.
Easy enough, right? I wasn't quite sure how these applications I wanted to restrict were being used, but I was pretty sure some of them were being used on the corporate network. I decided that initially I wanted to allow access to my internal private IP address range from these applications but deny access to everything else. This would solve my problem of these apps downloading code from some random site on the internet, hopefully without upsetting the IT cart at my organization. So I had two problems to solve. First, writing the allow/deny rules, and second finding out where the default action was for the WFwAS. I decided to start with PowerShell.exe, which was easy enough to test using the Invoke-WebRequest cmdlet.
Since I didn't like the complexity and openess of the default rule set, I cleared all of the default firewall rules. I then added in my rule to allow PowerShell.exe access to the internal network range. Problem one solved.
Now on to problem two. After looking around a bit I found out that the default action can be set by right clicking "Windows Firewall with Advanced Security..." in the WFwAS console and selecting "Properties". The default for Outbound connections was set to "Allow (default)". Since I had removed a whole list of rules I knew that switching this to "Block" was not an option. If I did, I would kill things like DHCP and DNS and various other critical traffic unless I explicitly listed each app and service and what they were allowed to get to. At this time I just wanted to restrict PowerShell.exe. I left the default action to allow and then went back to the "Outbound rules" and set out to configure a Deny to mimic the IOS example above. I figured I would just allow PowerShell.exe to the internal network, deny PowerShell.exe to Any, get them in the right order, and then let the default action tackle the rest.
I guess that means I was back to problem one. Just a minor setback though. I already had an allow rule, so I added in my deny rule for any traffic from PowerShell.exe to destination Any. I was able to get the rule order correct on the screen by deleting and re-adding the allow rule, and started my testing. (Those of you with experience with WFwAS will know exactly what happened next.) Access to the internet was successfully blocked!!! So far so good. Next I wanted to make sure access to my internal network was also allowed. Easy enough, quick test to a webserver on 192.168.40.11...
 |
| Interesting... |
And with that wall of red text I was introduced to WFwAS rule processing order of operations. I have worked on at least 7 major firewall/router vendors, all of which process rules from top down, first match wins. So why didn't it work? Simply put, WFwAS doesn't process rules that way. In fact, the order listed in the console didn't seem to make any difference at all. So, I went to the interwebs and hit the search button and landed on TechNet. Here is the WFwAS rule processing order, in summary:
- Windows Service Hardening (huh?)
- Connection security rules (IPSEC... I knew a little about this from a coworker)
- Authenticated bypass rules (more IPSEC magic)
- Block rules
- Allow rules
- Default rules
In my case it was the last 3 that really mattered (hopefully more on the first three in a later blog). WFwAS processes all of the Block rules, and if there is a match the traffic is denied. It then processes all of the Allow rules, and if there is a match the traffic is permitted. If there is no match, it applies the Default action defined in the properties dialog box.
With my PowerShell example, even though I had a more specific allow rule ordered before a broad deny rule, the deny rule was processed first and denied all of my PowerShell traffic and there was never an opportunity to match the allow I had set.
Whahh??
To date this is still the only firewall I have come across that processes rules in this way. It took me quite a while to get comfortable with the idea. I would love an hour with the committee at Microsoft who came up with this, um, most interesting solution. I tell myself it made sense at the time, right? I hope it has something to do with some dependency I don't yet understand.
So, my first attempt failed. After the initial elation I was a bit deflated. Perhaps I could switch to a rule that allowed all apps access to the internal network, things like web browsers access to all of the internet, and PowerShell to just the external ranges I knew it needed, and use a default action of "Block" at the end? This would be the "allow list" approach. I knew it would work, but I didn't know which applications needed access to the internet outside of web browsers. I knew that there were things like "web ex"perience meetings and meetings that I could "go to" that would need access to all sorts of IPs and that had random names and various hard drive locations they were launched from. I also knew that lots of installers relied on web connectivity to download applications. In short, I just wasn't ready for a pre-defined allow list, and I really just wanted to limit access to PowerShell and a few other applications.
I had my problem before me. Allow access to internal network for restricted apps, allow access to some external IP address ranges, block all else - without processing block rules first, with a default action of "Allow" for the rest (with logging enabled to start building my allow list - I hope to have more on this later as well). I was stumped and hungry and it was late and I was frustrated with Microsoft and I wanted to go home and see my family. I shelved my skunkworks project for a few days and mulled it over in the back of my head.
Turns out there is a way to do what I wanted, but I had to stop thinking like a firewall admin and think outside of the allow range. But, this post is already longer than I expected, so I will plan to go over how that was accomplished next week. I'll see if I can keep a cadence of a post a week.
Until then, work hard and spend time with your family.
Branden
@limpidweb
Tuesday, September 27, 2016
Should that app use the internet?
One of the inspirations for this blog has been sharing my research in mitigating different types of malware, or activity that can bypass mitigations and perform undesired functions. One thing that really caught my interest is the work that has been published by Casey Smith (@subTee). I found his work on using obscure functions of allowed applications to download code from the internet and execute it particularly interesting. For an example, see http://subt0x10.blogspot.com/2016/04/bypass-application-whitelisting-script.html.
I decided to take a stab at this. My first attempt was to use a technology I was familiar with to see if I could prevent the applications from using the internet to download code. I knew that the ASR mitigation in EMET could limit access to DLLs for an application, and based off of other ASR work I had done I suspected that a DLL was used in the network transaction at some point so I started pursuing this path. A coworker was able to set up a web server that had a customized version of subTee's regsvr32 download payload. Armed with a working example and Process Monitor with a filter to show DLLs (https://technet.microsoft.com/en-us/sysinternals/processmonitor.aspx) I went to work.
After a little work I was able to narrow down 2 DLLs that I think would work. Previous examples on Twitter targeted the example DLL but were easily bypassed (https://twitter.com/thechrisharrod/status/725713658848882688) because they only blocked one DLL that was not required for the download to execute. After some digging with Process Monitor I found out that the two DLLs that seemed to be the best matches were winhttp.dll and webio.dll. I don't know a whole lot about the DLLs themselves but my theory is that winhttp.dll was used to gather any proxy server settings (learned this from my time spent managing a proxy server) and webio.dll was used when making the actual web calls. If either of these were blocked with ASR I was able to get EMET to prevent regsvr and other applications from using the internet. WinHTTP appeared to have the best logging with the EMET blocks, so I targeted that, and it worked!!!
I began testing the mitigation for a few apps that had documented bypasses that used the internet that I thought had no business using it. After only a few hours of testing I knew that while effective, this was not going to work at scale. Simply put several of these applications were using these DLLs for internal network communications as well as for legit internet activity (who knew rundll32 was used to check OCSP?). My goal was to limit these, but to also grow into things more likely to use the internet like PowerShell, cscript, wscript, and mshtml. I had a tool that was effective, but it wasn't granular enough to allow some approved access and block the rest. It was effective, but only on or off.
So, I was back to the drawing board with a network on/off switch in my back pocket. After a few more weeks of work and thinking I found something that had potential, but I am out of time for now... so I will plan to address that on my next post. Maybe at some point in the future this will come in handy, only time will tell. I will see if I can get a video demonstrating the EMET mitigation posted at some point.
Until then, work hard and spend time with your family.
Branden
@limpidweb
I decided to take a stab at this. My first attempt was to use a technology I was familiar with to see if I could prevent the applications from using the internet to download code. I knew that the ASR mitigation in EMET could limit access to DLLs for an application, and based off of other ASR work I had done I suspected that a DLL was used in the network transaction at some point so I started pursuing this path. A coworker was able to set up a web server that had a customized version of subTee's regsvr32 download payload. Armed with a working example and Process Monitor with a filter to show DLLs (https://technet.microsoft.com/en-us/sysinternals/processmonitor.aspx) I went to work.
After a little work I was able to narrow down 2 DLLs that I think would work. Previous examples on Twitter targeted the example DLL but were easily bypassed (https://twitter.com/thechrisharrod/status/725713658848882688) because they only blocked one DLL that was not required for the download to execute. After some digging with Process Monitor I found out that the two DLLs that seemed to be the best matches were winhttp.dll and webio.dll. I don't know a whole lot about the DLLs themselves but my theory is that winhttp.dll was used to gather any proxy server settings (learned this from my time spent managing a proxy server) and webio.dll was used when making the actual web calls. If either of these were blocked with ASR I was able to get EMET to prevent regsvr and other applications from using the internet. WinHTTP appeared to have the best logging with the EMET blocks, so I targeted that, and it worked!!!
I began testing the mitigation for a few apps that had documented bypasses that used the internet that I thought had no business using it. After only a few hours of testing I knew that while effective, this was not going to work at scale. Simply put several of these applications were using these DLLs for internal network communications as well as for legit internet activity (who knew rundll32 was used to check OCSP?). My goal was to limit these, but to also grow into things more likely to use the internet like PowerShell, cscript, wscript, and mshtml. I had a tool that was effective, but it wasn't granular enough to allow some approved access and block the rest. It was effective, but only on or off.
So, I was back to the drawing board with a network on/off switch in my back pocket. After a few more weeks of work and thinking I found something that had potential, but I am out of time for now... so I will plan to address that on my next post. Maybe at some point in the future this will come in handy, only time will tell. I will see if I can get a video demonstrating the EMET mitigation posted at some point.
Until then, work hard and spend time with your family.
Branden
@limpidweb
Tuesday, September 13, 2016
Hello World
One of the tasks I get to perform at work is to research and study malware and try to find ways to mitigate it and minimize the damage it can do. I am tasked with assessing our defenses and where necessary providing additional layers for my organization to block malicious activities from occurring on workstations or servers without getting in the way of legitimate work.
I have been in several organizations where pen testers had already demonstrated that they could send attachments or get people to click on links to executable files that would bypass traditional defenses such as IPS, email filtering, URL filtering, sandboxing, and anti-virus. After that they were a command away from downloading .exe, .js, .dll, .reg or a host of other persistence mechanisms and free to do their work through covert C2 channels. Malware that was being blasted to us through spam campaigns or delivered through exploit kits was behaving similarly.
I have worked on traditional defense mechanisms for several years. I have a networking background and have spent a considerable amount of time trying to win this battle from the network infrastructure side, but find myself frequently bumping up against the limitations around trying to write policies that can effectively block this kind of activity. Don't get me wrong, I believe that IPS and firewalls and URL filters and such are an important defense mechanism and can effectively block many of the off-the-shelf attacks. But if something is targeted or just happens to fall within the range of addresses that I had to allow out from my workstations I frequently found myself unable to write a policy that was granular enough to stop it. Firewall/IPS/Proxy vendors have been working to fix this but they haven't cured the problem yet. There is a lot of malicious activity that is simply well behaved at the network layer. On top of that, things like custom encryption, new ciphers, or psychedelic obfuscation was limiting the effectiveness of the policies I did have and even updates several times a day weren't fast enough to keep up with the latest attacks.
Over time I have realized that winning the security battle is going to have to take place in large part on the endpoints. Managing a worm outbreak in my environment exposed me to the power of endpoint enforced policies. For a while only allowing pre-defined applications to run proved to be a big help and I became convinced that this would be one of the most effective ways of preventing this malicious activity. The next big thing for me was anti-exploit, and I dove into tools like Microsoft EMET. These are all still very effective, but the adoption of PowerShell by malicious actors flies right through many of the mitigations I had in place, and folks like Casey Smith are finding all sorts of ways to skirt around the limitations of these technologies.
My purpose with this blog is to explore different mitigations that I find (if any) to address these issues. I like to share my work (where I can) with the intent of helping the blue team and making contributions back to the security industry. Sometimes my thoughts will be partial or a work in progress. Sometimes it will just be lamenting how a mitigation didn't work. Sometimes they will just be about random things that seem cool at the time. Maybe the purpose will grow or change over time. Hopefully I can keep it coherent and the blue team finds it useful.
-Branden
@limpidweb
I have been in several organizations where pen testers had already demonstrated that they could send attachments or get people to click on links to executable files that would bypass traditional defenses such as IPS, email filtering, URL filtering, sandboxing, and anti-virus. After that they were a command away from downloading .exe, .js, .dll, .reg or a host of other persistence mechanisms and free to do their work through covert C2 channels. Malware that was being blasted to us through spam campaigns or delivered through exploit kits was behaving similarly.
I have worked on traditional defense mechanisms for several years. I have a networking background and have spent a considerable amount of time trying to win this battle from the network infrastructure side, but find myself frequently bumping up against the limitations around trying to write policies that can effectively block this kind of activity. Don't get me wrong, I believe that IPS and firewalls and URL filters and such are an important defense mechanism and can effectively block many of the off-the-shelf attacks. But if something is targeted or just happens to fall within the range of addresses that I had to allow out from my workstations I frequently found myself unable to write a policy that was granular enough to stop it. Firewall/IPS/Proxy vendors have been working to fix this but they haven't cured the problem yet. There is a lot of malicious activity that is simply well behaved at the network layer. On top of that, things like custom encryption, new ciphers, or psychedelic obfuscation was limiting the effectiveness of the policies I did have and even updates several times a day weren't fast enough to keep up with the latest attacks.
Over time I have realized that winning the security battle is going to have to take place in large part on the endpoints. Managing a worm outbreak in my environment exposed me to the power of endpoint enforced policies. For a while only allowing pre-defined applications to run proved to be a big help and I became convinced that this would be one of the most effective ways of preventing this malicious activity. The next big thing for me was anti-exploit, and I dove into tools like Microsoft EMET. These are all still very effective, but the adoption of PowerShell by malicious actors flies right through many of the mitigations I had in place, and folks like Casey Smith are finding all sorts of ways to skirt around the limitations of these technologies.
My purpose with this blog is to explore different mitigations that I find (if any) to address these issues. I like to share my work (where I can) with the intent of helping the blue team and making contributions back to the security industry. Sometimes my thoughts will be partial or a work in progress. Sometimes it will just be lamenting how a mitigation didn't work. Sometimes they will just be about random things that seem cool at the time. Maybe the purpose will grow or change over time. Hopefully I can keep it coherent and the blue team finds it useful.
-Branden
@limpidweb
Subscribe to:
Posts (Atom)



